| Product: AlphaWave | Category: Attack Surface Management |
| Company: AlphaWave | Review date: April 2021 |

This review is part of the April 2021 assessment of the Attack Surface Management (ASM) product category. If you haven’t read the category overview, you might want to check it out – it explains the category’s basics, use cases, and the general value proposition. Our testing methodology explains both how we interact with vendors and how we tested these products. In short, ASM products aim to discover and manage an organization’s external digital assets. This approach extends far beyond assets with an IP address, however, including everything from certificates to S3 buckets to DNS misconfigurations.
Company background
AlphaWave was founded in 2019 by Cody Pierce (CEO) and Mark St. John (COO), based in Austin, Texas. Both founders have extensive backgrounds in running services and product management for various high-profile vendors. Cody has an offensive security background and Mark has the defensive security background – a well-balanced founder formula!
AlphaWave is currently bootstrapped, though being in a popular market (ASM) and Austin-based, it’s only a matter of time before the VCs come knocking.
Product summary
AlphaWave is targeting the risk analysis and prioritization end of the ASM market. The product collects information on assets and attempts to identify issues and vulnerabilities. These findings are then prioritized for the customer.
AlphaWave is sold in three tiers: basic, advanced, and enterprise. The differences between the three are typical of tiered subscription products. Higher tiers get better support, more integrations, longer data retention, and more seats. For all but the smallest shop, we recommend the advanced offering for one big reason – AlphaWave’s team-focused features. Some of AlphaWave’s most compelling features involve working with a team within the application and we often advocate for teams to work on vulnerability management together.
Target market: AlphaWave’s product will work fine for an SMB/SME budget and a staff of one, but we feel it will really shine in the mid-to-large enterprise space (2k-10k users). Get much above that and customers tend to start demanding odd stuff that bloat and break products. (Note: this is our opinion, not anything AlphaWave has told us)
Time-to-value: Initial results show up within hours, like most other ASM vendors.
Maintaining value: As with other products (even ones that do seed discovery), it’s necessary to occasionally revisit seed selections and ensure they match what the company currently owns. Aside from that, the product doesn’t require any regular maintenance.
Total cost: The advanced tier will cost $27,000 when paid annually and basic costs $5,400 (but only allows for a single user). Assuming a large enterprise with roughly 5,000 employees, 500 exposed IP-based assets and a security team of 60, we’d recommend the advanced tier.
For initial setup and configuration, we’d estimate eight hours of analyst time to get things going, get familiar with the product, hunt down asset owners and start sending them triage emails. Add an additional two hours of senior analyst time to step in and help analyze some of the initial results for a total labor cost of $538.46. We think junior analysts could probably handle assigning asset owners and triaging findings going forward and estimate four hours of work per week to triage new findings, inquire about the status of existing ones and keep seed values updated. That brings the annual maintenance labor total to $6,999.20. Putting together product costs, deployment labor costs and maintenance labor costs, the estimated total cost of ownership comes to $34,537.66 for our hypothetical large enterprise.
Strengths: Comfortable UI, innovative features and accurate results.
Weaknesses: Lacks some features seen at this price or lower, like seed discovery (though, admittedly, those products lack some of AlphaWave’s features – this is a difficult market for direct comparisons).
Conclusion: An impressive debut for a young company and a product we’re eager to see grow and improve over the next few years.
Deployment and configuration
As with other ASM platforms, the initial seed values are provided at account setup. Once the account is ready a welcome email gets you logged in and set up. Part of the initial account setup kicked off asset discovery and scanning, so we already had results by the time we logged in.
Before digging into the UI, we wanted to add some other team members and double-check the seed domains and networks to ensure we didn’t leave anything out. Clicking Organization takes you to these settings. Additional teammates can be added, given a role (admin or user), a title, bio and even tags. We imagine tags would be perfect for listing department or subsidiary names. Seed domains and networks can also be added or managed here.
One final initial configuration option to consider are what AlphaWave call “Pipelines”. Input pipelines are used to pull additional assets from public clouds or other sources of asset data. It took us just a few seconds to connect AlphaWave to an AWS instance using an AWS key pair. Outputs could be used to send AlphaWave’s findings to a SIEM, SOAR tool or perhaps to Microsoft Teams or Slack as an alternative to sending email notifications when new findings pop up. The importance of getting security data where it needs to go is important in an age where we already have too many dashboards, workflows and emails.
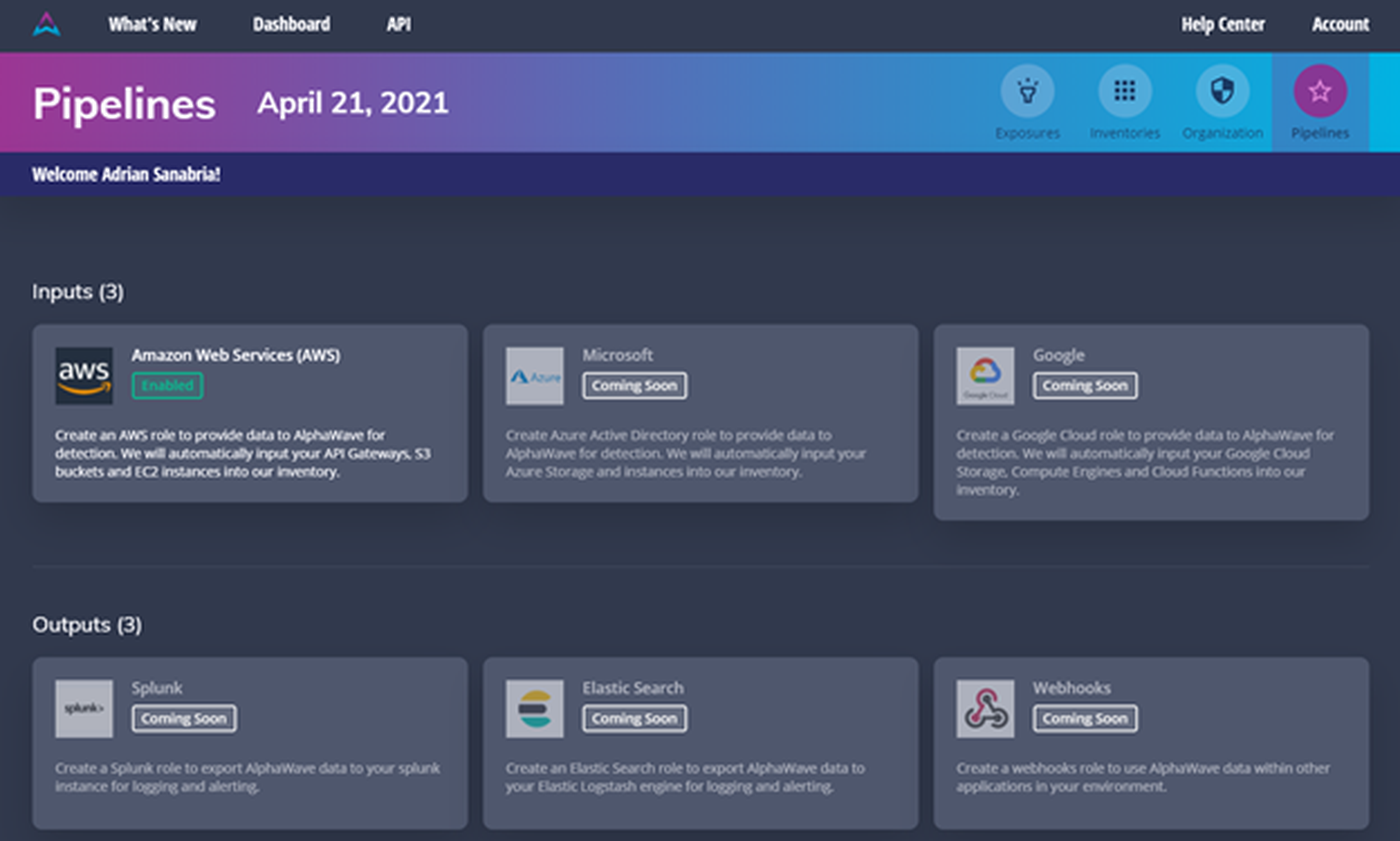
Usage
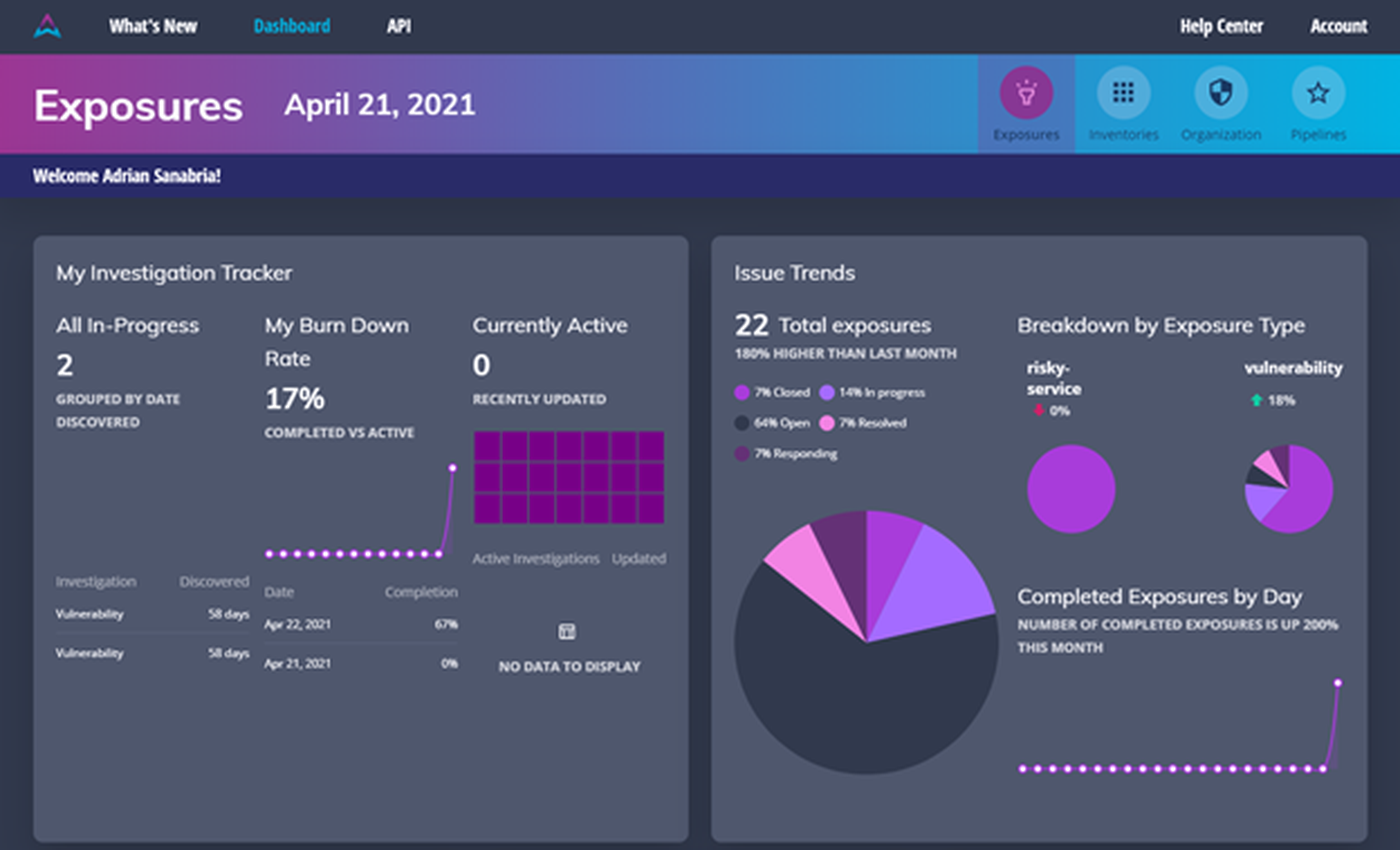
AlphaWave has a refreshingly unique look and UI. Like other ASM products, logging in lands us on a dashboard. We get some progress metrics, some summaries and totals. There are also some ‘bang for your buck’ style dashboard widgets as well, pointing to the most common vulnerabilities and the most vulnerable hosts.
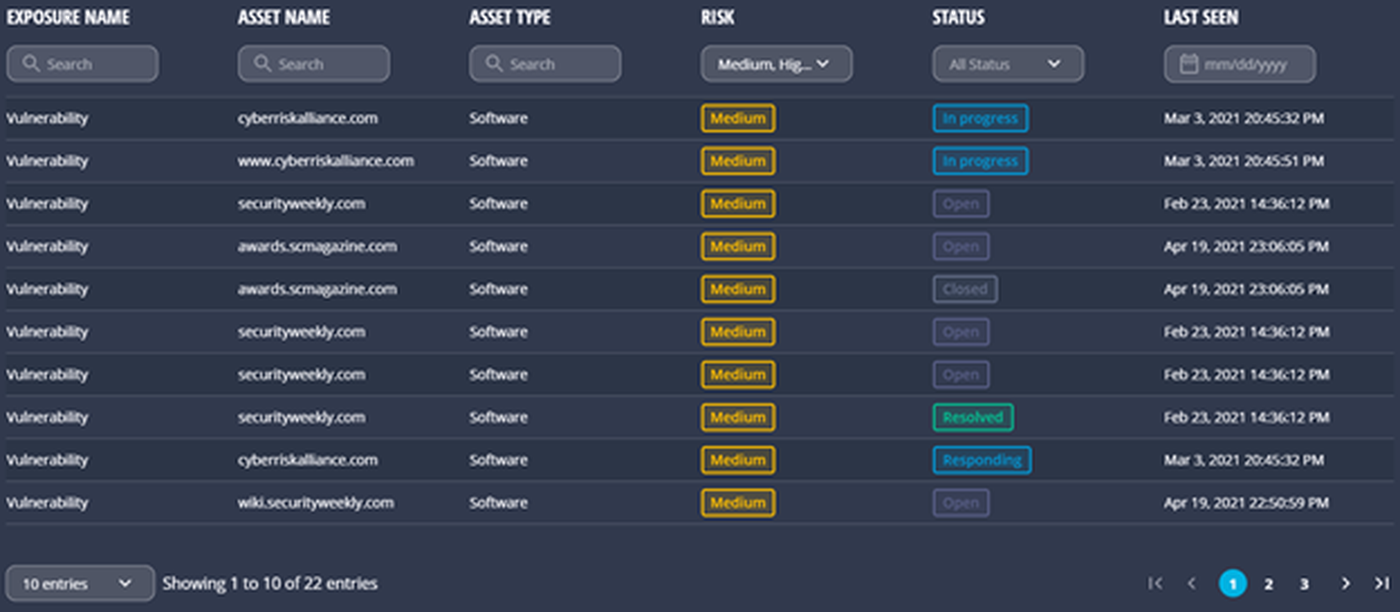
We scroll down to find a list of vulnerabilities with their corresponding asset names, risk levels and current status. While we could do with a multi-select option and perhaps some more detailed data in this view, the column-specific filters work well to narrow down to what you need. App performance is good - it responds quickly to filtered changes.
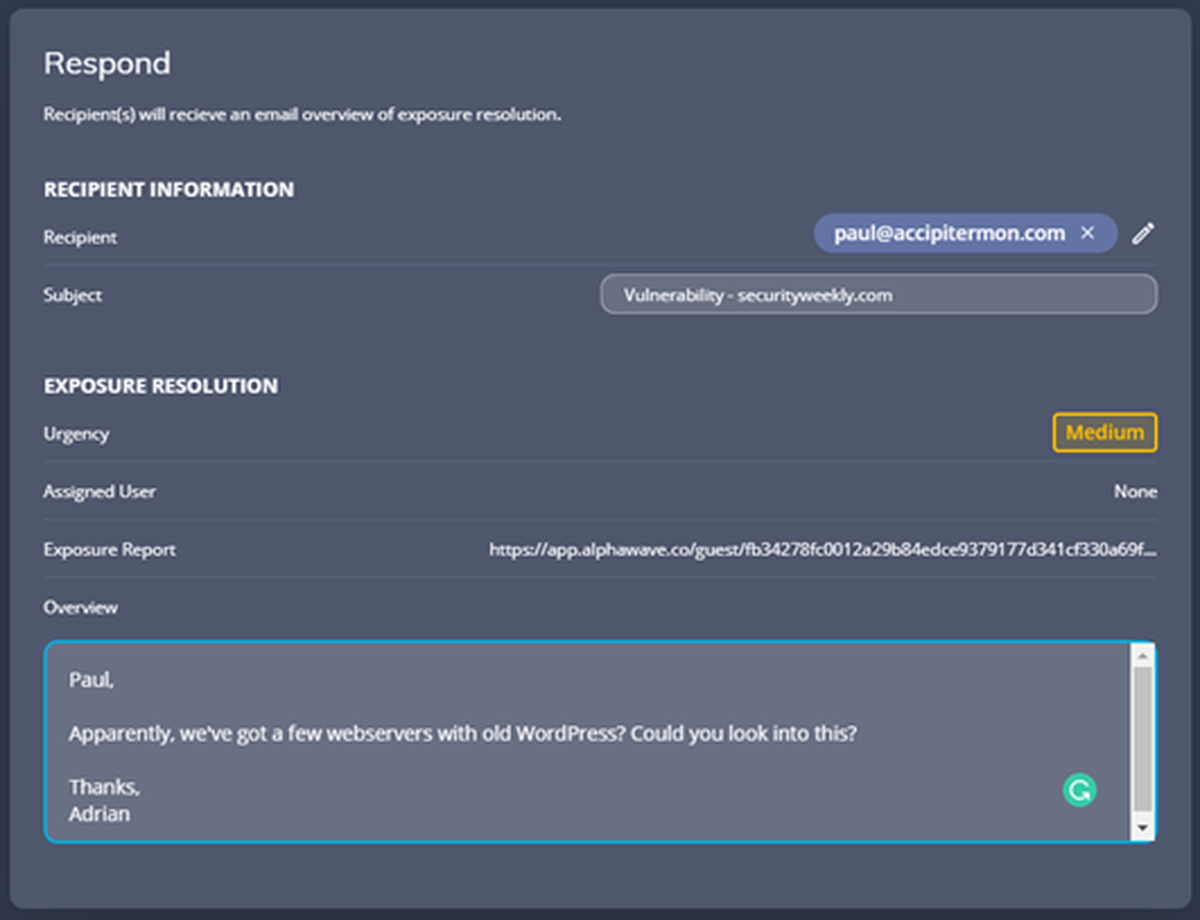
When drilling down into one of these findings, there’s a lot to discuss. Some of what you’d expect to see are here – vulnerability details, custom tagging, issue status, asset ownership, and issue assignment are all common to see in ASM products, or even vulnerability management products. What is unique is the embedded workflow you find around mid-page, which AlphaWave refers to as the Exposure Triage Workflow. We’ll explain part of it, but they have a 2-minute explainer on YouTube as well (we’re suckers for short explainers).
- Validate Exposure
- Validate Inventory
- Respond
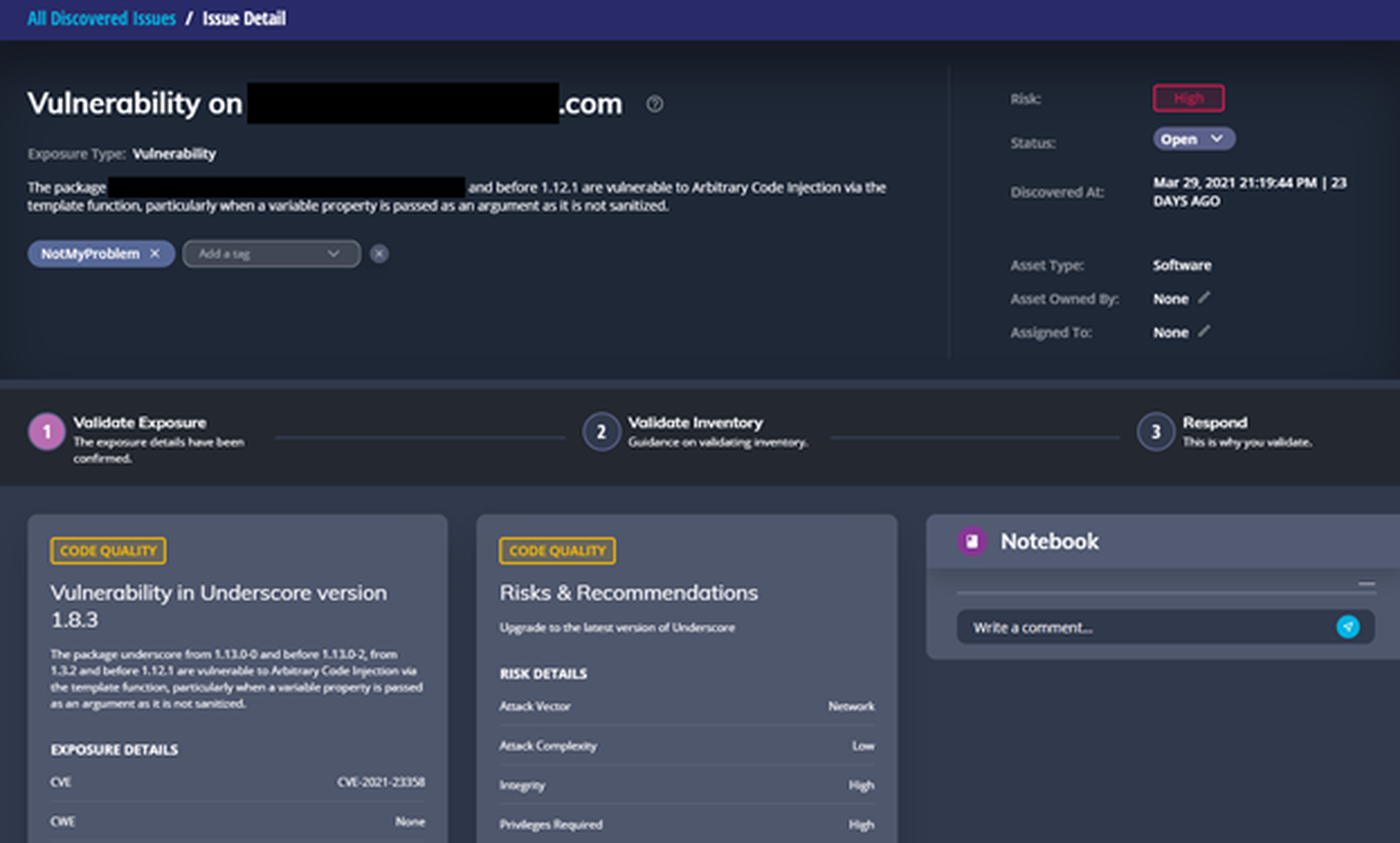
So fine, the workflow walks you through the process of understanding the vulnerability (step 1), determining the asset owner (step 2), but in step 3, there’s the ability to email anyone a read-only link to this particular issue! Sending an email seems far from revolutionary, but it’s all about workflow.
If you have a few dozen issues to triage that might belong to three or four people, you’re going to be doing a lot of screenshotting, typing, and window switching back and forth between an email client. This is easier, faster, and makes so much more sense. We’re always advocating for getting other teams logins into vulnerability management tools to allow them to manage issues related to their own assets (which you can also do with AlphaWave), but this is a great alternative.
Perhaps AlphaWave found an issue in a third-party product and you need to get the details over to their support folks? Drop the support email into this form, set the status to “Responding” and off it goes. Download as CSV and Export to PDF has long been the answer to sharing data in security products, but a share this page option that sends a read-only link is a refreshing alternative. It works for Google Drive, Office 365, and Dropbox – why not security tools?
Also, note in the screenshot above that there’s also space (called Notebook) to leave comments on each issue – another opportunity for team collaboration and communication.
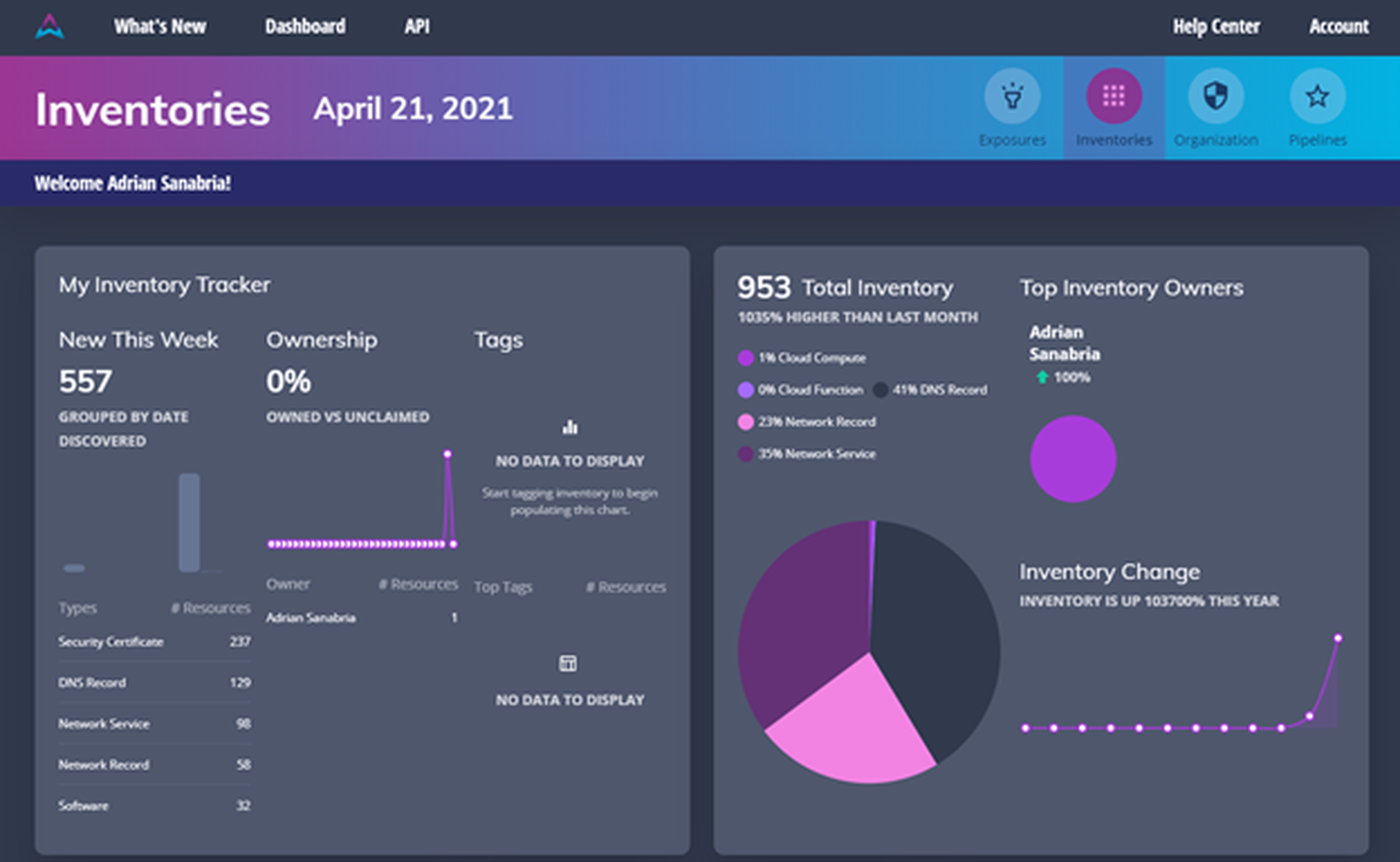
The inventory view details all the assets collected. Again, there are some graphs showing totals, breakdowns by type and trending data, which are always helpful. Breakdowns by owner and tag are also here.
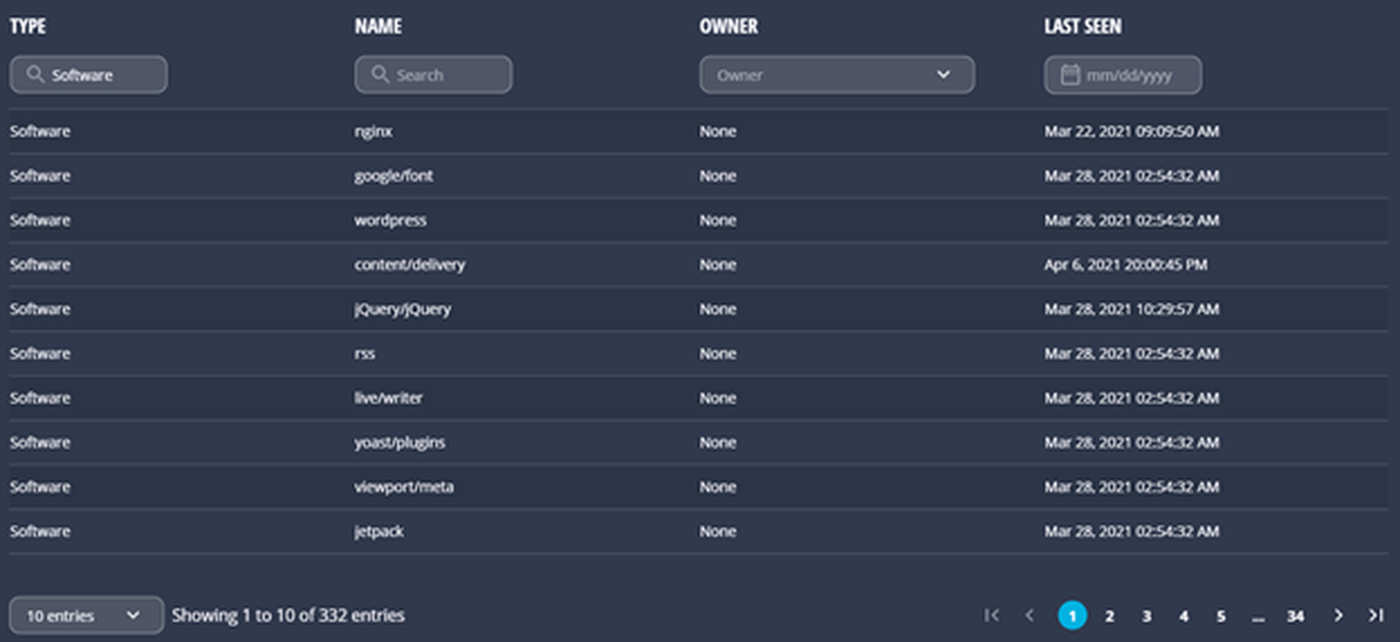
Again, a list of assets with the ability to filter on each column is available further down the page.
Performance
We’re not doing any formal performance testing in this round of ASM product reviews (we will next time), but at a glance, AlphaWave seemed to find roughly the same true positives other ASM products discovered, with little, if any false positives.
Claims
Claim 1: “Use AlphaWave to continuously visualize and manage your attack surface, before attackers do.”
This statement is essentially the core value prop for all ASM and is well put – no issues here.
Claim 2: “Better inventory, better security”
Amen.
Security program fit
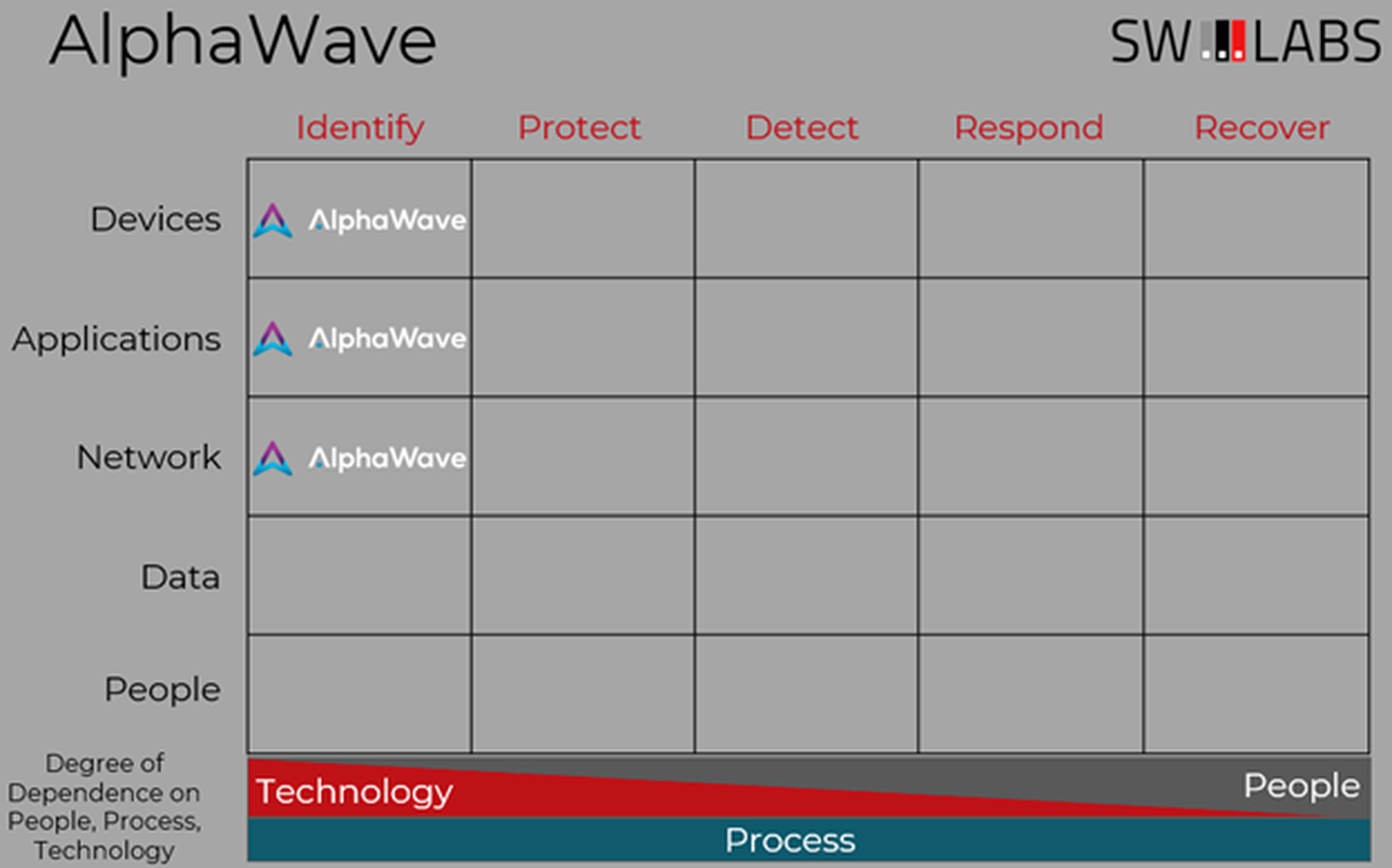
AlphaWave, like other products focused on discovering vulnerabilities and misconfigurations, fits solidly within the Identify column of the Cyber Defense Matrix.
Conclusion
AlphaWave may lack some more advanced features, like seed discovery (the ability to discover domains that were not original seed entries, but still belong to the organization), but for a young product bootstrapped by a two founder team, it’s an impressive start that punches well above its weight class.
Innovative features like Pipelines and the built-in Exposure Triage Workflow set this product apart from other vendors in this market.



